We were at MOA one sunday and Jill received a smishing (SMS phishing) attempt. I’d like to share with you these screencaps to explain what smishing is, how it’s done, what the malicious actor’s goal is and how to avoid getting smished. Yes I like the word smish i’m using it a lot here.
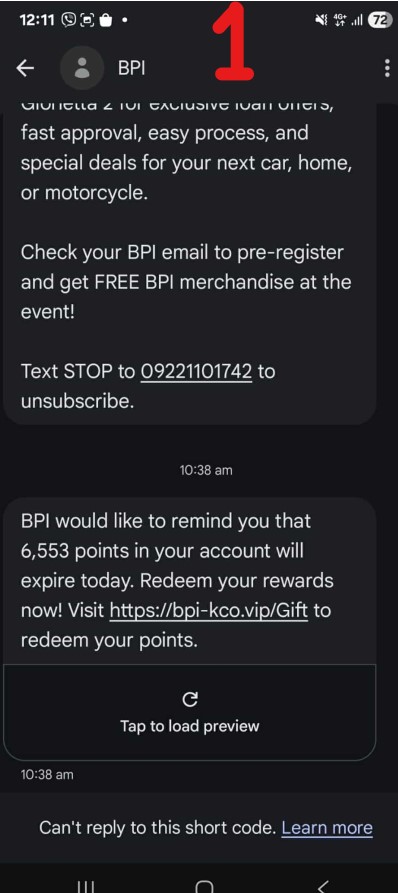
So Screencap #1 is a fake email made to look like it came from BPI. I dont know if BPI sends SMS of any sort but if they do, the sender possibly copied most of it and then added the last paragraph ‘BPI would like to remind you that..’ and it includes a URL. Take note of that URL.
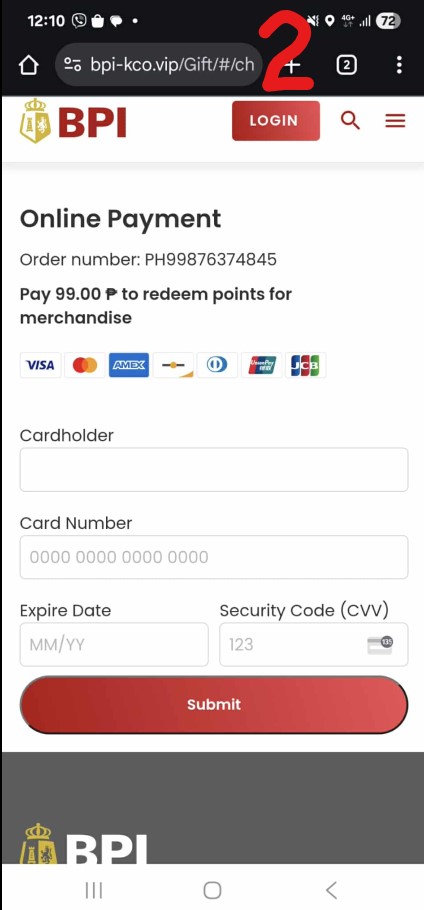
Screencap #2 is of the website that loaded after the URL was clicked. Again, it looks like a legit BPI website with an online credit card payment form including the usual name, cc no., Expire(sic) Date and CVV.
Ok some answers:
HOW IS IT DONE?
Malicious actors send these bulk emails using fake cell towers. Fake cell towers, some portable, were created initially for such things as setting up temporary communications after typhoons or earthquakes destroy infrastructure to help establish initial communication. Phones ‘attach’ to these towers after which then are will receive messages en masse. I’ve added a link in the comments to a related event. I understand though (not sure), that these are restricted by distance, and so it MIGHT BE (again, not sure) in the trunk of some roving car. If so, it would make sense that this happened at MOA on a Sunday, to try and get as many victims as possible. I also understand it costs half a million pesos, but tech prices as we all know always drop over time and besides smishing probably has a great ROI.
WHATS THE GOAL?
The goal is to trick recipients to click the link thinking they might win something, enter their CC details after which they will try to buy stuff with it. Keep in mind, credit card authentication systems are still pretty tough and most will call or email you if they detect suspicious purchases, so the malicious actors still need to try and get through that. Smaller purchases will probably get through though.
HOW TO AVOID?
Remember the URL? That is a dead giveaway. If BPI is actually running a promo this way, which is highly unlikely to begin with, it will do it using its own well established BPI.COM.PH domain. To date, there is NO WAY you can spoof (pretend) to be another site whilst using the same domain. What I mean is that if you type BPI.COM.PH on your browser, you should get the Bank of the Philippines Islands website and nothing else.
Web Development is my turf. One of the best reasons to have a website is to establish a literal ‘home’ on the web. Companies and individuals use their website as a way to prove ownership of all its activities. It’s far more powerful than a social media page. For example anyone can make a fake BPI facebook page, attaching images and even stealing content from the original one to make it legit. But if you quickly check their website and the facebook link is different from the one posted there, its an automatic fake.
Having a website makes sure that any news, activity, promos, announcements etc., floating around can be easily authenticated. For a huge bank like BPI, if it isn’t announced on their website, it’s bogus.
In this case and again, if BPI is going to run an online promo, it will do so on its BPI.COM.PH website and official social media. They will never use some weird link like in these screencaps, it makes no sense after they’ve worked so hard to keep their domain and website legit.
So again, if the URL . is . pointing . to . something . else, its . 1000% a . Scam.
Oh one more thing, ‘Expire Date’ is spelled wrong, so again that is a super dead giveaway. Marketing teams are paid millions to get these right so a typo is highly unlikely. But this is a negligible error, people may ignore that because they’re too excited to win a prize.
FINAL NOTE
I said it before in the past, the fact that SMS can be spoofed is terrible, devastating news for all of us. SMS used to to be a far more trustworthy messaging solution between two individuals who already trust each other. Much more than IM, Viber, etc. messages, which are all stored on a server somewhere which can always be prone to man in the middle attacks, or conventional hacking by someone with access to those servers. I suppose it was just a matter of time, but its still stings me that it had to happen.
I suppose the solution is that phone IMSI needs to be strengthened via encrypted authentication protocols to telco registered, legit towers, kind of like the way SSL works on browsers, but that’s a major phone and telco industry overhaul that may have to be justified by earnings from SMS, which are probably minimal if any.
I actually want to talk to telco industry and phone people about what they could do about this, I genuinely think its a tragedy. Maybe I should start a podcast about these things.